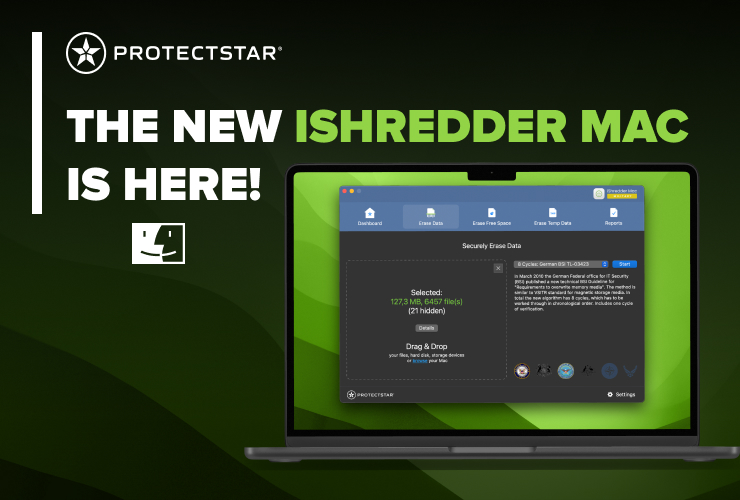
iShredder™: Military-Grade Data Shredding for Ultimate Privacy and Security

In a world where data breaches and identity theft are increasingly common, ensuring that your personal and sensitive information is deleted securely is more important than ever.
Enter iShredder™, the most popular iOS, Android, Windows, and Mac data shredder app. Trusted by defense departments and government agencies, this app offers military-grade data deletion that makes data recovery impossible. Whether a beginner or a professional, iShredder™ provides the tools to safeguard your privacy.
Why iShredder™?
When you manually delete files such as documents or photos, this data can still be recovered from your device's free space until it has been securely overwritten using advanced deletion algorithms. iShredder™ ensures that your files or storage space are overwritten according to patented security standards, making data recovery impossible in just three simple steps.
You might be surprised by what data still lingers in your device's free memory. This is because when you delete a file manually, the operating system only removes its association with that file, leaving the data itself in memory. The corresponding sector is marked as "free," allowing another file to use this memory block again. iShredder™'s "Securely delete free memory" function helps you overwrite this free memory space securely, ensuring that previously deleted data cannot be recovered.
Certified Deletion Algorithms:
iShredder™ boasts over 20 approved erasure algorithms, exceeding international government and military security standards for secure data erasure. In addition, authorities and independent organizations have analyzed each deletion method for its security and effectiveness in ensuring safe data destruction.
Erasure algorithms available in iShredder™ include DoD 5220.22-M E, U.S. Air Force (AFSSI-5020), U.S. Army AR380-19, DoD 5220.22-M ECE, BSI/VS-ITR TL-03423 Standard, BSI-2011-VS, BSI TL-03423, NATO Standard, CSEC ITSG-06, HMG InfoSec No.5, DoD 5220.22 SSD, and more.
It is essential to understand the different deletion algorithms offered by iShredder™ and how they help ensure the security of your data. For example, the DoD 5220.22-M E algorithm, which the U.S. Department of Defense widely uses, overwrites data multiple times with different patterns, making it virtually impossible to recover the information. Other algorithms like the NATO Standard or the U.S. Army AR380-19 use similar techniques to overwrite data, ensuring your sensitive information remains secure and unrecoverable.
Selling or Giving Away Your Device?
If you plan to sell or give away your smartphone, tablet, P.C., laptop, or Mac, securely erasing the data stored on your device is crucial. Even seemingly deleted data such as notes, passwords, address books, photos, WhatsApp messages, videos, calendars, and favorites can be quickly recovered from your device's memory. iShredder™ ensures that your data is securely erased and unrecoverable by third parties, protecting your privacy and safeguarding your sensitive information.
Why Regular Deletion is Not Enough:
More than regular deletion methods is required when protecting your privacy and the sensitive information stored on your devices. Standard deletion processes leave behind traces of your data, which can be easily recovered using specialized software or hardware tools.
iShredder™'s military-grade secure deletion methods go above and beyond the typical deletion processes, overwriting your data multiple times to ensure it is completely unrecoverable. By using iShredder™, you can be confident that your sensitive information remains secure and protected, even after it has been deleted from your device.
Erasure Reports:
iShredder™ doesn't just securely delete your data; it also provides you with an erasure report that you can use and archive as proof of deletion. These reports offer auditable and verifiable assurance that all data has been purged according to published standards such as GDPR, U.K. Government InfoSec No. 5, U.S. DoD, and NIST 800-88. This is especially important for businesses that must comply with data protection regulations and individuals who want to maintain their privacy.
iShredder™ offers a range of customizable settings and features to suit your specific needs. For example, you can choose from multiple deletion algorithms based on your desired level of security or adjust the number of overwrite passes to balance speed and effectiveness. With iShredder™, you have complete control over the data deletion process, ensuring that it meets your unique requirements for privacy and security.
In addition to personal use, iShredder™ is an invaluable tool for businesses and organizations that handle sensitive data. Companies can use iShredder™ to securely delete customer information, financial records, and other confidential data, ensuring that it cannot be recovered and misused by unauthorized individuals. By incorporating iShredder™ into their data management practices, businesses can protect their reputation, comply with data protection regulations, and reduce the risk of costly data breaches.
iShredder™ is designed to be user-friendly, making it accessible to beginners and experienced users. Its intuitive interface lets you securely delete files, folders, or free memory space with just a few taps or clicks. In addition, step-by-step instructions guide you through the deletion process, ensuring that you can easily and confidently use iShredder™ to protect your privacy.
Whether you're an individual looking to protect your personal information or a business seeking to maintain compliance with data protection regulations, iShredder™ is the ultimate tool for secure data deletion.
Download iShredder™ today and take control of your privacy and security.
Learn more: https://www.protectstar.com/en/products/ishredder