

Neueste Artikel

The fateful sale of a hard disk
Not every success story has to be positive. Unfortunately, this story of Thomas was no exception:In ...

iShredder™: Military-Grade Data Shredding for Ultimate Privacy and Security
In a world where data breaches and identity theft are increasingly common, ensuring that your person...

The Growing Trend of Taping Webcams: Privacy Protection Lessons from Snowden, Comey, Zuckerberg, and Others
Discover why influential figures such as Edward Snowden, James Comey, and Mark Zuckerberg tape their...

Safeguard Your Privacy with Camera Guard™: The Comprehensive Protection for Your Device
The Camera Guard™ app provides robust camera and microphone security, ensuring your privacy remain...

So deaktivierst Du versteckte Facebook-Bloatware auf Deinem Android-Smartphone: Schütze Deine Privatsphäre und optimiere die Leistung
Bloatware bezeichnet unerwünschte, vorinstallierte Apps, die von Geräteherstellern, Mobilfunkanbie...

Warum ist die Firewall AI-App nicht mehr im Google Play Store verfügbar? Die unerwartete Sperrung unserer Firewall AI-App
Die überraschende Entfernung einer App, die von Hunderttausenden Nutzern als wertvoll und sicher an...
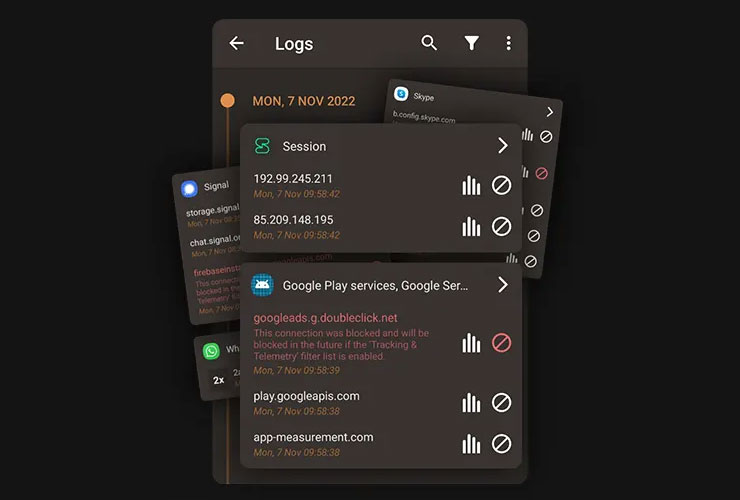
Making the Most of Firewall AI: Two Tips to Enhance Your Device
The internet has become an indispensable part of our lives. We rely on it for everything from social...

Defending Digital Freedom: How a Journalist Used AI-Powered Security Tools to Thwart Surveillance and Protect His Privacy
Ahmed, a journalist in a third-world country, was concerned that he might be under surveillance. He ...

Hiding in Plain Sight: How Malware Can Be Concealed Using Steganography in Images?
In cybersecurity, attackers constantly evolve and develop new ways to conceal malicious code within ...

Wie sicher ist die Löschung von Dateien? Eine Analyse der Wiederherstellungschancen von Dateien
Wie sicher ist die Löschung von Dateien? Eine Analyse der Wiederherstellungschancen von Dateien auf...

So schützt du dein Android-Gerät vor SIM-Karten-Kloning
Hast du schon einmal einen Anruf oder eine Nachricht erhalten, die angeblich von dir stammen soll �...

Protectstar's AI-powered protection
Protectstar's AI-powered protection offers a wide range of benefits for users. The Deep Detective™...